Pay Attention to Cyber security Threats !!
Pay Attention to Cyber security Threats !!
It is becoming increasingly challenging to keep up with emerging cyber threats that are even more dangerous and destructive than their forerunners. Time and again, we are reminded of how difficult it is to keep our IT environments secure in the face of highly sophisticated cyber attacks.

Let’s start off with some of the most recent cyber security threats and then we’ll discuss a few of the measures that organisations should put in place to minimize the associated security risks.
Phishing attacks:
Phishing is a form of fraud in which an attacker masquerades as a reputable entity or person in email or other forms of communication. Attackers will commonly use phishing emails to distribute malicious links or attachments that can perform a variety of functions. Phishing scams typically employ social engineering to steal user credentials for both on-premises attacks and cloud services attacks.
Phishers can use public sources of information to gather background information about the victim’s personal and work history, interests, and activities. Typically, through social networks like LinkedIn, Facebook, and Twitter. These sources are normally used to uncover information such as names, job titles and email addresses of potential victims. This information can then be used to craft a believable email.
The attack is then carried out either through a malicious file attachment, or through links connecting to malicious websites. In either case, the objective is to install malware on the user’s device or direct the victim to a fake website. Fake websites are set up to trick victims into divulging personal and financial information, such as passwords, account IDs or credit card details.

How to approach?
To help prevent phishing messages from reaching end users, our Layots Cyber security Experts recommend layering security controls, including: Antivirus software, Network Firewalls, Gateway Email Filter, SPAM filtering & Web Security Gateway. Layots offers strong encryption to keep the data secure in place and also while in transit.
The best practices to avoid various types of phishing includes..
- Turn on two-factor authentication (2FA) — This protective measure requires multiple pieces of information for someone to be able to log in. It requires two of the following:
- Something you know (a password, passphrase, etc.)
- Something you have (a mobile app, a smart card, a personal token, etc.)
- Something you are (bio-metrics such as a retinal scan, fingerprint, etc.)
- Using a sender policy framework (SPF) — This is a type of email validation system that allows domain managers to authorize specific hosts to use a domain.
- Verifying suspicious communications through official channels — If you receive a phone call from someone claiming to be your bank, hang up and call your bank directly using the phone number on the back of your card. If you receive an email from someone claiming to be the CEO who wants you to transfer money, send sensitive data or anything else even remotely suspicious, call them or their assistant on an official company phone line. Don’t ever rely on the contact information provided in a suspicious communication.
- Using websites that are secure and encrypted — Ensure that your website — and those that you visit — are secure and encrypted. This means visiting websites that use secure protocols (HTTPS) instead of insecure ones (HTTP). You can secure your website using SSL/TLS Certificates, which protect the data that is transmitted between your site and your end-users’ web browsers.
Remote Worker Endpoint Security
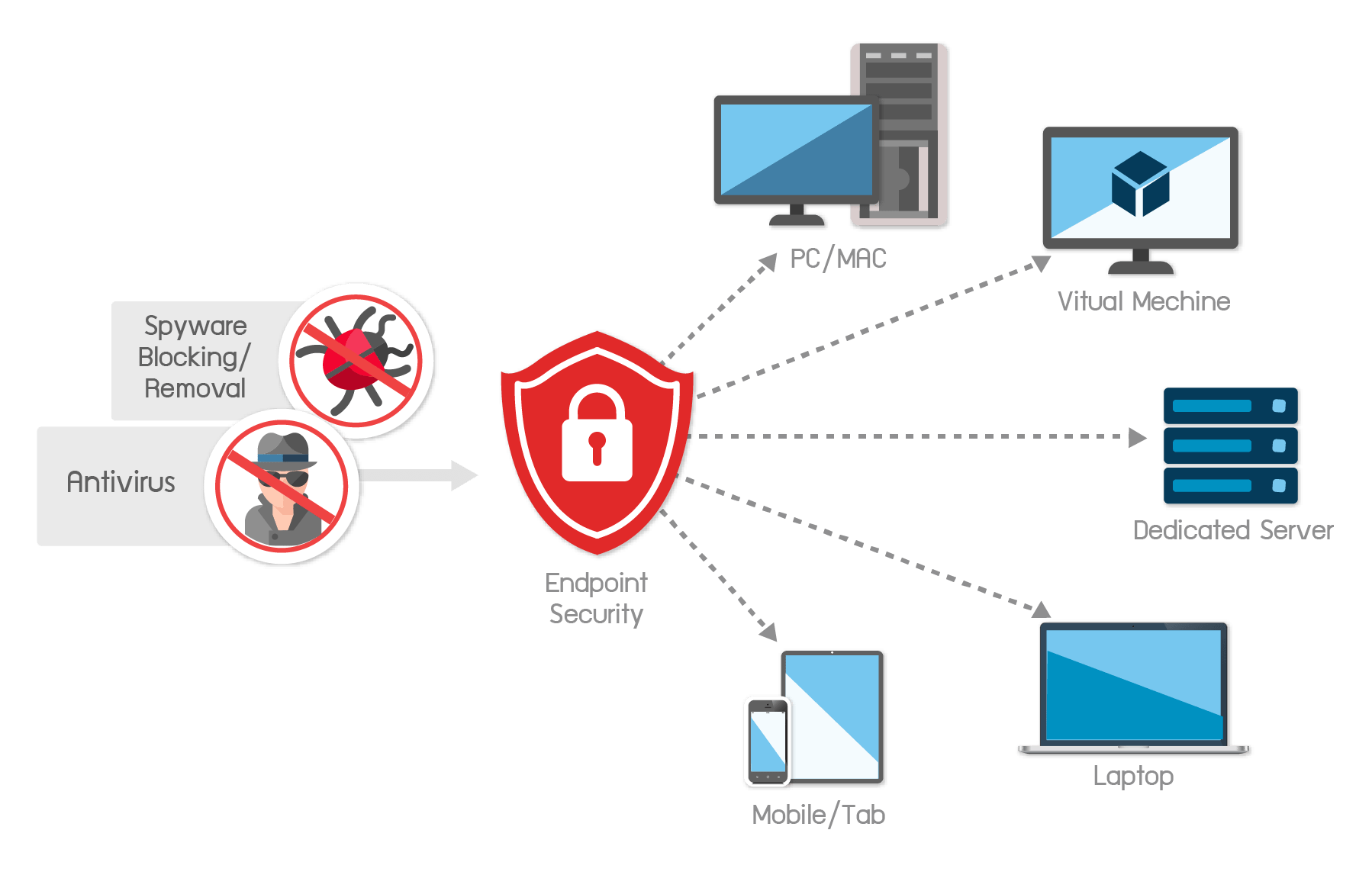
Endpoint security is the process of protecting individual devices with the broader aim of securing the network and the data of the organization. In any given organization, endpoints are on the front line of the security war. With IT professionals required to monitor and manage hundreds of thousands of endpoints across multiple networks, the chances of missing security vulnerabilities increase exponentially.
How to approach?
Endpoint Detection and Response (EDR): An EPP is usually an integrated suite of security technologies, such as antivirus/anti-malware, intrusion prevention, data loss prevention and data encryption, to detect and prevent a variety of threats at the endpoint.
An EDR differs from traditional antivirus and anti-malware. It takes a proactive approach by not only detecting suspicious activity and malware, but also by keeping the network safe by containing threats to an endpoint in case of an incident. EDR tools protect endpoints by monitoring events, gathering data and analyzing it to reveal potential cyber-threats and issues. They detect anomalies in endpoints by identifying rare processes, risky occurrences, and strange connections, which are mostly flagged based on baseline comparisons.
Dedicated DLP Software: Data loss prevention, or DLP, is a term that refers to strategies for preventing the leaking or the destruction of company data, especially confidential data. DLP software stops data from going out, instead of guarding against theoretical attacks. It does this by redacting or tokenizing outgoing information, or by blocking risky user actions. DLP systems can also detect unauthorized access of sensitive data, which could be a sign that someone is attempting to move or copy data to an environment that is not managed by the organization the data belongs to.
DLP is also growing in importance due to newer and more stringent regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), that heavily penalize companies for leaking customer data.
The best practices to secure your endpoint includes..
- Setup VPN on your remote endpoints to allow your users to access a secure link back to the office environment.
- Automate patching of your off-network devices, monitor the patch status on all machines and track the vulnerabilities that can impact your environment
- 2FA provides a second layer of authentication to access your applications by requiring users to provide a password (something they know) and a mobile app or token (something they have). 2FA is one of the easiest methods you can use to prevent cyber criminals from taking advantage of weak or stolen credentials (passwords) and hacking into your systems.
- Protect end-user data without the hassle of setting up an appliance or local storage at every office location. Use Cloud Backup to back up from anywhere with internet connectivity—including Wi-Fi, so the data on remote endpoints is covered as well.
To know more about the best practices and how to protect your endpoint devices, discuss with our Layots Cyber-security Experts.
IoT devices:
Cyber-criminals are constantly searching for vulnerabilities in business networks, home computers, and now IoT devices for opportunities to steal information, extort businesses, and take control of computer systems remotely. IoT devices open up a whole new world to hackers and cyber-thieves. The responsibility falls on those implementing the technology to take all the necessary precautions to include appropriate safeguards.
The best practices to combat IoT Cyber Threats includes..
● Implement network-level security to authenticate individual IoT devices. This prevents unrecognized requests from being accepted.
● Ensure compliance with regulations such as HIPAA for medical data or Europe’s GDPR requirements. This includes managing and encrypting data efficiently.
● Enforce secure passwords and regular changes. Do not allow the retention of default passwords for IoT devices.
● Include network architecture devices in IoT planning. Firewalls and Routers are favourite entry points for hackers, as they are often neglected in password protection, patching, and software updates.
● Be prepared. No network, server, or IoT device is 100% free of vulnerabilities. The risk of being a victim of cyber-attack – or at least an attempted attack – is very real. Formulate a contingency plan that provides for data recovery, isolating impacted devices, and alternatives to conducting business when devices must be quarantined.
For more information on how Layots can help your business, healthcare institution, or other organization implement a comprehensive defence against IoT cyberattacks, Contact our Cybersecurity Professionals today.
Sophisticated Ransomware Attacks:

Ransomware attacks have become one of the most notorious cyber threats. In this attack, a hacker uses malware to encrypt data that may be required for business operations. An attacker will decrypt critical data only after receiving a ransom. The effects of a single ransomware attack can be extremely damaging to small and midsize businesses, leading to exorbitant costs associated with downtime and recovery.
Solutions like Advanced Threat Protection or Endpoint Detection and Response (EDR) provide behavior-based detection and blocking of ransomware attacks that go beyond the limitations of signature-based detection of known malware. Additionally, many enterprises implement application whitelisting to bolster ransomware protection efforts. This solution allows only specified applications to run, reducing the risk of ransomware programs executing on local machines.
Best practices to defeat ransomware attacks:
- Use anti-virus and anti-malware software or other security policies to block known payloads from launching.
- Make frequent, comprehensive backups of all-important files and isolate them from local and open networks.
- Install the latest security updates issued by software vendors of your OS and applications. Remember to Patch Early and Patch Often to close known vulnerabilities in operating systems, browsers, and web plugins.
- Segment your networks to keep critical computers isolated and to prevent the spread of malware in case of attack. Turn off unneeded network shares.
- Turn off admin rights for users who don’t require them. Give users the lowest system permissions they need to do their work.
- Restrict write permissions on file servers as much as possible.
- Stress the importance of examining links and attachments to make sure they are from a reliable source. Warn staff about the dangers of giving out company or personal information in response to an email, letter, or phone call.
- For employees who work remotely, make it clear that they should never use public Wi-Fi because hackers can easily break in through this kind of connection.
Learn more about the proper steps to prevent, detect and recover from ransomware, and you can minimize its impact on your business with the help of our Layots Cybersecurity Experts
Should a security breach occur, you need a robust action plan to efficiently deal with the breach and get your company back on its feet with minimum damage and as quickly as possible. The plan should include a communications strategy for both internal and external stakeholders, including customers, investors, and others. The more you prepare in advance, the better equipped you will be to deal with a crisis.
To explore how we can help build your organisation’s cyber resilience, please reach out to our cyber-security experts or write to us!!

Layots has 20+ years of unmatched experience in providing IT solutions. Our solutions offer speed, agility, and efficiency to tackle business challenges in the areas of data security, cyber security, service management, application development, automation, test & development environments and operations.

