Cloud Security : Planning Guide 2021
Cloud Security : Planning Guide 2021

Introduction
To manage cloud security in today’s world, you need a solution that helps you address threats to enterprise data and infrastructure, including the major trends you are up against. While information technology does move rapidly and with a degree of unpredictability, a comprehensive risk management approach, designed to flex and adapt, enables organizations to embrace cloud services with security confidence.
The structural foundation of this approach will not only assist in mitigating the risks associated with cloud deployments and usage, but also improve and standardize your security posture and practices across all your environments—public and private clouds as well as bare metal server clouds; and allow you to skip future security overhauls brought on by the emergence of new types of information technologies and security threats.

Compared to on-premises private data centres (i.e., traditional environment), cloud usage introduces incremental risk. Yet, as we propose, this escalation of risk is controllable such that the benefits and risks of using the cloud can be balanced. In essence, driving toward the same security objectives as in traditional environments is the right path when using the cloud.
Security is a split responsibility
Contrasting with the “fully owned and operated” foundation of traditional environments, in all three of the prevalent public cloud models—Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS)—security is a split responsibility between the cloud provider and its subscribers (tenants); with the level of responsibility in the hands of the cloud provider growing in moving across the models from IaaS to SaaS.
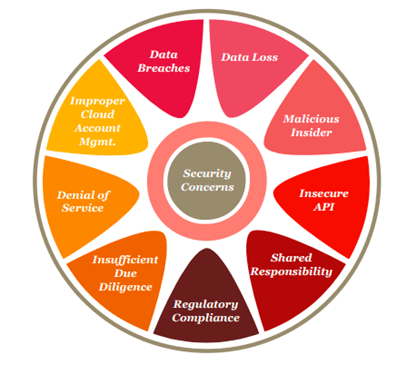
Similarly, visibility into the cloud provider’s security operations is not as deep or deterministic as in traditional environments. Consequently, cloud tenants are indirectly asked to trust without full verification. For example, vulnerability scanning, and remediation is part of the cloud provider’s security responsibilities (e.g., of virtual network interfaces and hypervisor in IaaS, and up through the application software in SaaS); but frequency and depth of vulnerability scanning, and prioritizing remediation, is determined by the cloud provider, not individual tenants. Similarly, identifying and mitigating security incidents and configuration errors attributed to the layers of the cloud infrastructure under the cloud provider’s purview are also outside the line-of-sight of the tenants. In cloud environments, the strength of security is partially dependent on the strength of the security operations and administration conducted by the cloud provider.

On-Premises Vs Cloud Security
Today, data is the key that drives the operations of departments. Such data helps keeping track of the performance, discover value adding insights, and improve security.
Data also plays a primary role in defining and outlining various IT security policies, be it on-premises or cloud setup. While some departments prefer in-house data collection and management, others opt for cloud migration because of its services availability and scalability. Cloud technologies have ensured easier management of data, especially ensuring enhanced data security. As the cloud ensures on demand infrastructure access, Departments are able to implement and maintain effective and efficient cloud security frameworks that can manage and tackle emergent threats. Differentiating between traditional IT security and cloud security is especially important. Each has its own set of advantages / limitations and being aware of both approaches will strengthen the Department’s operational decision making.
A traditional IT approach gives the department increased control over daily usage of each device. It is possible to monitor and control data along with daily data management and the data resides within department premises. Though an on-premises setup would need training of existing Department resources on emerging security technologies. However, the biggest challenge with traditional IT systems is the Capital Expenditure required to install and maintain the security components. Asset refresh for end-of-life security components would also add to capital expenditure for the departments. The department is tasked with the responsibility to manage and monitor security related compliances / certifications which in turn are capital intensive and would require internal capabilities within the Department. Hence gaps in the security related practices may give rise to vulnerabilities.
The cloud ensures easier data management and system security. Instead of controlling every aspect of data security control on-site, the Department can easily outsource the data security needs to a prominent and reputable Managed Service Provider.
Furthermore, most cloud developers are more experienced with advanced security and data governance models. This means that the Departments will be able to plan appropriate strategies to ensure real time risk mitigation. An important reason for the reluctance to move more data into the cloud are the concerns around security.
Where to Start?!
Typically, data does not stay in one place on your network, and this is especially true of data in the cloud. Encrypt your data wherever it is in the cloud: at rest, in process, or in motion.
Data in motion
• Data in flight over networks (Internet, e-commerce, mobile devices, automated teller machines, and so on)
• Data that uses protocols such as Secure Sockets Layer (SSL), Transport Layer Security (TLS), Internet Protocol Security (IPsec), Hypertext Transfer Protocol Secure (HTTPS), FTP, and Secure Shell (SSH) Data in process
Data in progress
• Transactional data in real time, or sensitive personal financial data stored as encrypted fields, records, rows, or column data in a database Data at rest
Data at rest
• Files on computers, servers, and removable media
• Data stored using full disk encryption (FDE) and application-level models
The principal security technologies and concepts needed to secure cloud environments include the following:
Segmentation & Isolation
Public cloud’s multi-tenancy demands that organizations establish and maintain virtual walls around each of their workloads and the network traffic that flows to and from workloads and among workloads. This effort is essential in shielding workloads and data from other cloud tenants and cloud administrators, and, from a performance perspective, assuring that the workload is not “crowded out” of its necessary compute, storage, and networking resources.
Depending on the workload, best effort performance is intolerable; verifiable service level agreements (SLAs) are essential.
Threat Detection and Mitigation
Threats designed to disrupt operations, undermine integrity, or eventually sow the seeds for data exfiltration are omnipresent. Cloud providers recognized this and have built threat detection and mitigation technologies and procedures into their operations to serve all of their tenants; and, naturally, to maintain service uptime and integrity. Yet, with the micro-targeting of advanced threats, the cloud provider’s threat detection is not a panacea. Adding a second layer of threat detection is an advisable practice for all cloud tenants to defend against the external threats that evaded the “for everyone” threat detection of the cloud provider.
Security Information & Event Management (SIEM)/Log Management
No defence will ever be completely impenetrable; there must be a backstop of non-stop collection of data to discover early warning signals of multi-stage exploits. Continuing on the same path as in traditional environments, next generation SIEM and Log Management forms this essential backstop in cloud environments. For maximum effectiveness, data collection must be broad, from the network layer up through the application layer; monitoring must be conducted on a real-time basis and produce outcomes that are grounded in context. In circumstances where a hybrid approach is used—a mix of private data centre (traditional environment) and public cloud—the SIEM and Log Management capabilities must seamlessly span both environments. Additionally, security intelligence must be equally comprehensive in spanning external and internal factors, in order to filter what can be a mountain of daily security issues to a more manageable, prioritized few.
Incident Response and Forensics
Despite best efforts to protect virtual workloads in cloud environments, the potential of a major security incident still exists and must be handled with expedience and prudence. While a noble aspiration, planning and rehearsal is critical to ensure that cool heads prevail during the heat of the moment. Forensics is also essential, to gauge the exploit’s extent and, of equal importance, to guide defence-tightening adjustments. Comprehensive SIEM and Log Management capabilities are essential in supporting both incident response and forensics.
Identity & Access Management
As previously stated, the remoteness (i.e., access from any device, from anywhere) of public cloud services, and the proliferation of SaaS subscriptions intensify the necessity of an Identity & Access Management (I&AM) system to control user access privileges across private and public environments. Automating subscriber management functions (i.e., bulk SaaS enrolments, self-service password administration, and revocation of access privileges for departed employees across all environments) are also important functions. Reporting on user log-in activity, also a function of I&AM, assists in discovering questionable activities by users and administrators, and in assigning the costs of cloud services to individuals and departments. Last, single sign-on lessens credential sprawl and user time spent in resetting forgotten passwords and logging into each SaaS subscription individually.
Data breach news stories are far too common; and, with certainty, there are countless more data breaches that are either undetected or not publicly reported. Several coordinated approaches assist in mitigating the risk of data breaches (e.g., segmentation and isolation, vulnerability testing, SIEM, and I&AM). Encrypting valuable data in all of its modalities—at rest, in motion, and in use—should also be used. Of equal importance, the cloud user’s
encryption keys should be inaccessible by the cloud provider, to eliminate the potential that the cloud provider can access tenant data, and to ensure that data erasure in the cloud is complete (i.e., by destroying the encryption keys)
Secure Software Development
Secure software development has long been advocated by security professionals as essential in systematically reducing the frequency and severity of software vulnerabilities. Considering the heightened exposure in public cloud environments, the importance of secure software development is equally heightened.
Vulnerability Scanning and Patch Management
Even with devotion to secure software development, vulnerable software still exists, if for no other reason than the threat actors continuously advancing their techniques. Also, other layers of software lie below (e.g., operating system) or to the side of applications (e.g., browsers, drivers, and readers), and are subject to vulnerabilities. Periodic vulnerability scanning and regular patch management is a good standard practice, and one that takes on greater importance in the consideration that vulnerabilities in the configuration of a virtual workload will remain with each new virtual instance of the workload, until the vulnerabilities are discovered and effectively removed from the workload’s configuration profile.
The Last Word! Security in a fast-paced technology-infused world cries for an “invest once and deploy everywhere” approach. For this to be realized, security must be planned in advance and built-in, yet still be fluidly adaptable to circumstances, and singularly controllable. Lacking this type of security approach, the practice of security in the cloud will be on a path of reactiveness, with expensive and sub-optimized operations.