Security Information and Event Management (SIEM) Solution & it’s importance
Security Information and Event Management (SIEM) Solution & it’s importance
SIEM stands for Security Information and Event Management. SIEM products provide real-time analysis of security alerts generated by applications and network hardware. It ranges from Log Management Systems to Security Log / Event Management, Security Information Management, and Security Event correlation. Security information and event management (SIEM) is an approach to security management that combines SIM (security information management) and SEM (security event management) functions into one security management system.
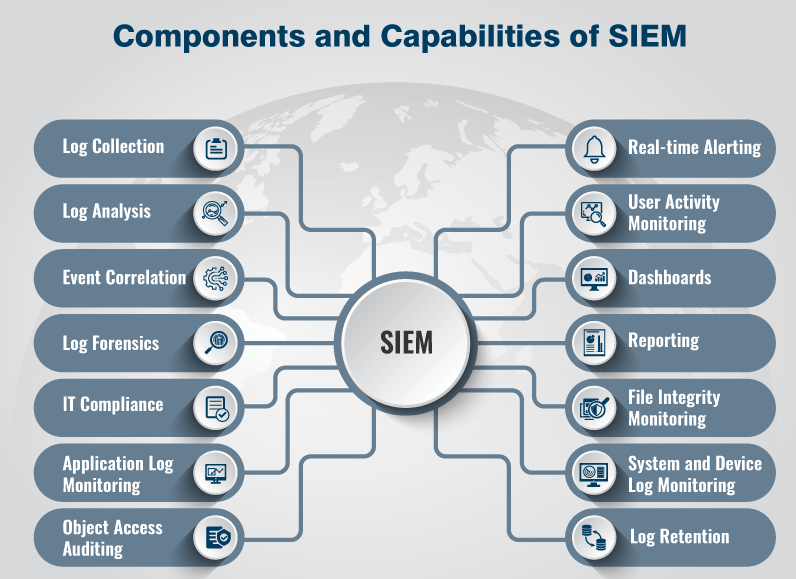
Need for monitoring the data
Today’s Modern SIEM solutions enable your company to react quickly and precisely in the event of a threat or data leak. Changes in the threat landscape have created a need to find a larger variety of threats faster. In addition, security operations teams are struggling to keep up with the deluge of security alerts from an increasing arsenal of threat detection technologies while relying on manually created and maintained document-based procedures for operations.
Fortunately, the new digitalization era and machine learning are creating new possibilities for SIEM solutions that are challenging the old definitions and domain areas for product categories. For businesses to establish an effective cybersecurity program, a Modern SIEM solution is a must-have. Today’s businesses need a solution that can unify, simplify, and automate what’s already there.
How does SIEM work?

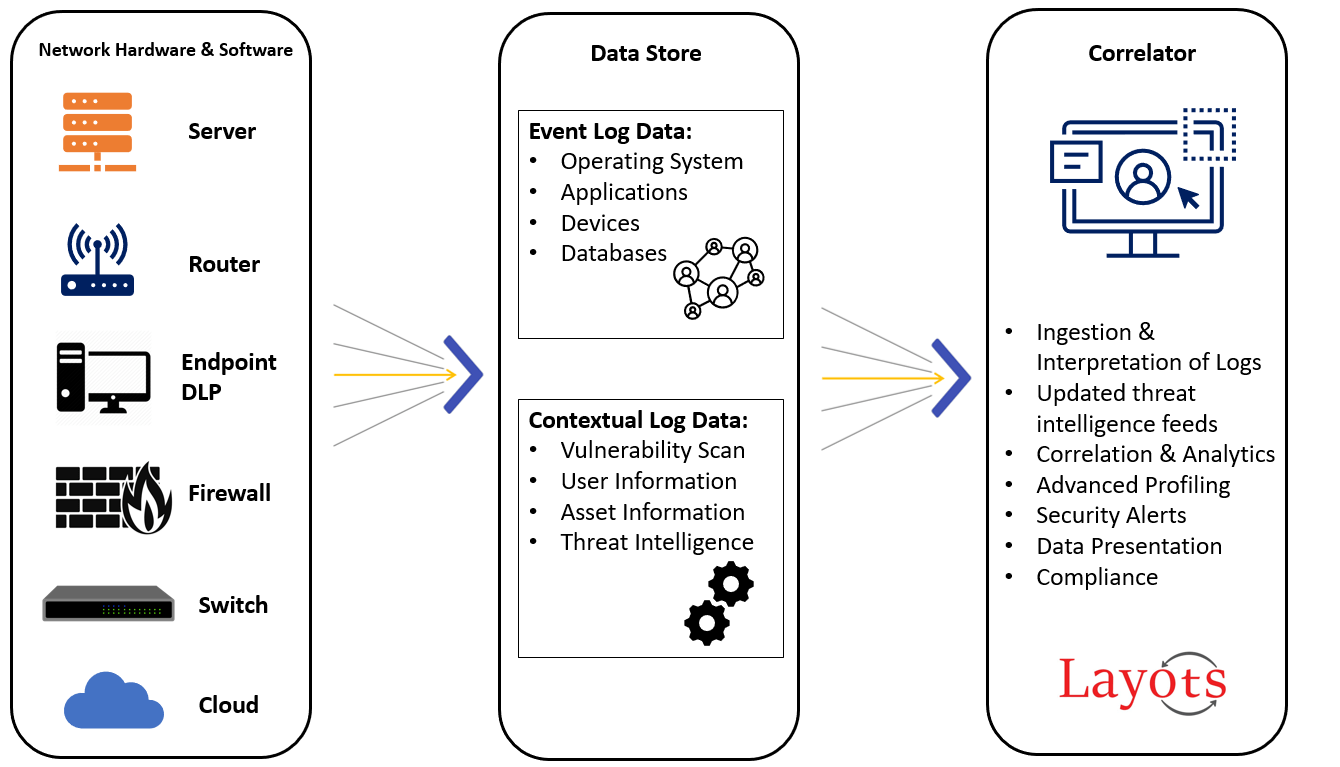
The underlying principles of every SIEM system is to aggregate relevant data from multiple sources, identify deviations from the norm and take appropriate action. For example, when a potential issue is detected, a SIEM system might log additional information, generate an alert, and instruct other security controls to stop an activity’s progress.
The security information and event management process can be broken down as follows:
- Data collection – All sources of network security information, e.g., servers, operating systems, firewalls, antivirus software and intrusion prevention systems are configured to feed event data into a SIEM tool.Most modern SIEM tools use agents to collect event logs from enterprise systems, which are then processed, filtered and sent them to the SIEM. Some SIEMs allow agentless data collection.
- Policies – A profile is created by the SIEM administrator, which defines the behavior of enterprise systems, both under normal conditions and during pre-defined security incidents. SIEMs provide default rules, alerts, reports, and dashboards that can be tuned and customized to fit specific security needs.
- Data consolidation and correlation – SIEM solutions consolidate, parse and analyze log files. Events are then categorized based on the raw data and apply correlation rules that combine individual data events into meaningful security issues.
- Notifications – If an event or set of events triggers a SIEM rule, the system notifies security personnel.
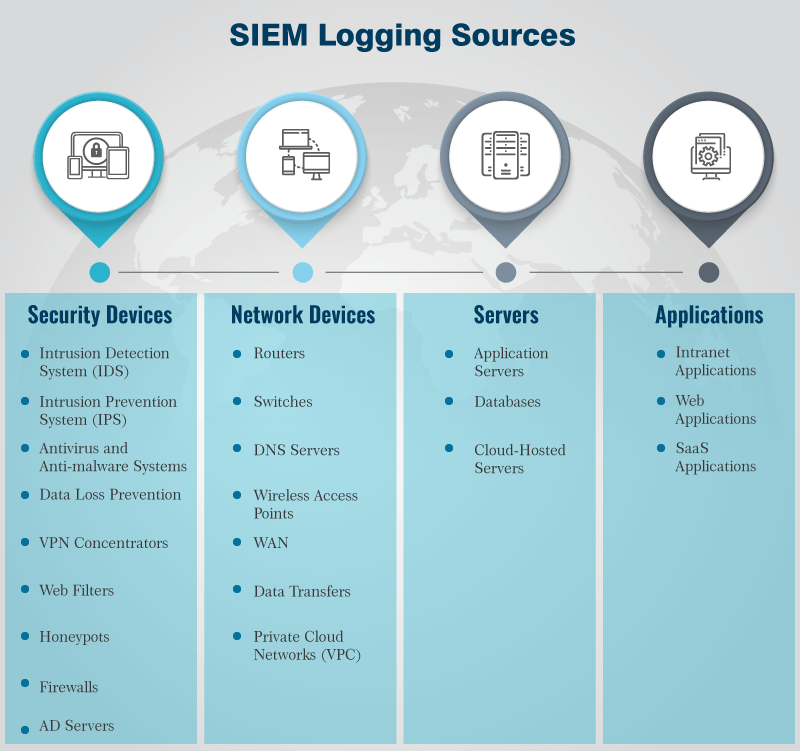
What are the effective SIEM logging sources?
Benefits of SIEM Solution:
- A SIEM system can also help an organization meet compliance requirements by automatically generating reports that include all the logged security events among these sources. Without SIEM software, the company would have to gather log data and compile the reports manually.
- You may be required to demonstrate compliance to PCI DSS, FISMA, FERPA, HIPAA, SOX, ISO, NCUA, GLBA, NERC CIP, GPG13, DISA STIG or one of many other industry standards. In general, most SIEM systems have some kind of onboard report generating system that will help you to conform to your compliance requirements.
- A SIEM system also enhances incident management by enabling the company’s security team to uncover the route an attack takes across the network, identify the sources that were compromised and provide the automated tools to prevent the attacks in progress.
- It shortens the time it takes to identify threats significantly, minimizing the damage from those threats
- It can be used by companies for a variety of use cases that revolve around data or logs, including security programs, audit, and compliance reporting, help desk and network troubleshooting.
- It can perform detailed forensic analysis in the event of major security breaches.
What to look for in an SIEM Tools?
Before choosing a SIEM tool, it’s important to evaluate your goals. For example, if you’re looking for a SIEM tool to meet regulatory requirements, generating reports will be one of your foremost priorities.
On the other hand, if you want to use a SIEM system to stay protected against emerging attacks, you need one with high functioning normalization and extensive user-defined notification facilities.
However, companies should look for SIEM tools that offer the following capabilities:
- compliance reporting
- incident response and forensics
- database and server access monitoring
- internal and external threat detection
- real-time threat monitoring, correlation, and analysis across a variety of applications and systems
- intrusion detection system (IDS), IPS, firewall, event application log, and other application and system integrations
- threat intelligence and
- user activity monitoring (UAM)
By providing a simplified overview of your IT infrastructure you can make impactful business decisions. We have a history of success in IT security and safeguarding businesses from risk and mitigating reputational and financial damage. We ensure less business downtime by enabling your team to respond and detect threats faster and efficiently. The SIEM solution integrates easily with all devices in your network, giving a holistic and correlated overview of events in your IT infrastructure.

Layots has 20+ years of unmatched experience in providing IT solutions. Our solutions offer speed, agility, and efficiency to tackle business challenges in the areas of data security, cyber security, service management, application development, automation, test & development environments and operations.

