Virtual Desktop Infrastructure (VDI) | Deployment
The term Virtual Desktop Infrastructure (VDI) was originally coined by VMware and has since become an accepted technology acronym. Presenting virtualized applications and desktops to users is universally referenced as end-user computing (EUC).
Virtual desktop infrastructure (VDI) is a desktop virtualization technology wherein a desktop operating system (OS) runs. VDI hosts desktop environments on a centralized server and deploys them to end-users on request. VDI segments the servers into various virtual desktops which the users can access remotely through their devices. It is either managed in an on-premises or in cloud data center.
The virtual desktop image is delivered over a network to an endpoint device, which allows the user to interact with the operating system and its apps as if it were running locally. The endpoint may be a traditional PC, thin client device or a mobile device. As far as the users are concerned, VDI gives you the freedom of accessing your desktop from anywhere at any time through a VDI client software.
Persistent vs. non-persistent VDI deployments
Persistent VDI:
Under persistent VDI, a user always logs into the same desktop image, with all changes to its applications and data retained. That allows for full personalization. In contrast, non-persistent VDI does not save any changes.
Persistent VDI works as follows:
- A user is assigned a standardized desktop from the resource pool the first time they log on
- Each subsequent time they access the VDI environment, they are connected to the same desktop, with all of their changes retained in the virtual OS image even after the connection is restarted
- For workers with complex and fast-paced digital workflows, this means they can easily pick up where they left off and benefit from extensive personalization of the desktop’s virtual apps and settings
Non-persistent VDI:
In contrast, non-persistent VDI works as follows:
- The end client may be connected to the same desktop every time or to a randomized one from the pool
- In either case, no changes are saved upon restarting
- A nonpersistent VDI implementation is well-suited to one-off access to a desktop but not to using a virtual desktop exactly like a personal physical equivalent, which requires persistent VDI
Since nothing is saved once the connection is terminated, IT does not have to maintain a large number of customized OS images, allowing for simplified data center management and reduced costs. Non-persistent VDI also streamlines the management of devices for kiosk and task workers who don’t need to save anything.
Components of VDI
1. Virtualization:
Virtualization is the technology that divides the system architecture into different layers. Before virtualization, the hardware was bound to the operating system (OS) at the time of installation. Thus, in the case of a hardware failure, the OS also crashed, and you would lose all the data. Through virtualization, the OS and the underlying hardware are separated by software called hypervisor. You can install multiple operating systems on a hypervisor installed server.
2. Hypervisor
Hypervisor is software that separates the operating system from the underlying hardware. The hypervisor creates a virtualized environment in which the hardware can be divided into multiple virtual machines (VMs). Each virtual machine can have its unique configuration, OS, and applications.
In VDI, the hypervisor creates desktop instances in these VMs. Each desktop instance can act as a separate desktop and can be provisioned to the users. The High Availability (HA) function in the hypervisor also lets it connect to multiple servers. Hence, even if a physical server fails, your desktop instance is moved to another server almost instantaneously.
3. Connection Broker
Connection broker is a software program that connects the users to the desktop instances. It is also responsible for the authentication of the users and sending them to their desktop instances.
The connection broker also keeps track of active and inactive desktops. When a user sends a request to connect to a desktop, it provides the user with an idle desktop instance. When a user disconnects desktop, it updates the status to inactive.
How VDI does the magic?
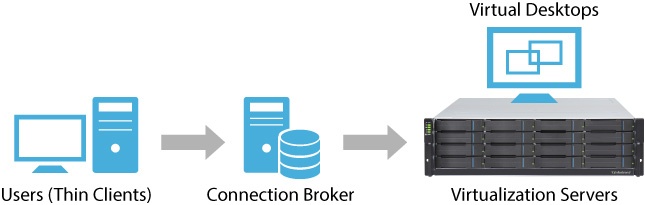
In VDI, When the user logs in to their desktop from the client software, the request is accepted by the connection broker after authentication. The connection broker (which is a software-based gateway that acts as an intermediary between the user and the server) then analyses the request and sends the user to their desktop in the desktop pool. The hypervisor segments server into virtual machines that in turn host virtual desktops, which users access remotely from their devices. Users can access these virtual desktops from any device or location, and all processing is done on the host server.
Each virtual desktop presented to users may be based on a 1:1 alignment or a 1: many ratios, which is often referenced as multi-user. For example, where a single virtual desktop is allocated to a single user, this would be considered 1:1, but where numerous virtual desktops are shared under a single OS, this would be referenced as a hosted shared model or 1: many.
Security in VDI

It is necessary to secure user communications with the Secure Sockets Layer (SSL)/Transport Layer Security (TLS) protocols. By utilizing a virtualized environment for your VDI implementation, it does not grant non-authorized users’ access to the management console itself. Every action is tracked through a management interface, which is perfect for PCI and HIPAA compliance requirements.
Centralized data is easier to manage, as you have only one entry point. That makes patch management much easier, as you do not have to worry about a multitude of devices in every office. It also simplifies project management and user profile management, which are essential for maintaining high data security levels. Your IT department will enjoy full control over centrally managed Microsoft apps and virtual desktops, enabling them to pre-configure security policies based on user roles.
With a centrally managed system, a disaster recovery plan must be taken into consideration. Centralized data should be replicated offsite for a greater level of safety.
Pros of VDI Solution

- Device Portability: VDI technology enables you to access your desktop from various devices. You can use mobile, laptops, tablets, or thin clients to view your desktop. Bring your own device (BYOD) programs mesh well with VDI. Where users are bringing their own endpoint devices into the workplace, fully functioning virtual desktops eliminate the need to integrate apps within the user’s personal physical device. Instead, users can quickly access a virtual desktop and use enterprise applications with no additional configuration.
- Security: Since all the data lives in the data center, not on the endpoint, there are significant security benefits of VDI. A thief who steals a laptop from a VDI user cannot take any data from the endpoint device because there is no data stored on it.
- Accessibility: The most distinguishing feature of VDI is remote access. With VDI, you can access your desktop from anywhere, day or night. the ability to more easily support remote and mobile workers. Mobile workers comprise a significant percentage of the workforce, and remote workers are becoming more common. Whether these individuals are field engineers, sales representatives, on-site project teams or executives, they all need access to their apps while traveling. By presenting a virtual desktop to these remote users, they can work as efficiently as if they were in the office.
- Cost savings: Since processing is done on the server, the hardware requirements for end devices are much lower. Users can access their virtual desktops from older devices, thin clients, or even tablets, reducing the need for IT to purchase new and expensive hardware.
- Centralized management: VDI’s centralized format allows IT to easily patch, update or configure all the virtual desktops in a system.
Prime Players in the market!!
There are three prime players in the VDI market: Citrix, Microsoft, and VMware. Of these, Citrix’s VDI product, formerly Xen-Desktop (holds the largest market share), followed by VMware Horizon and then Microsoft Remote Desktop Services (RDS).
Session protocols Each endpoint device must install the respective client software or run an HTML 5 -based session that invokes the respective session protocol. Each vendor offering platform is based on a display protocol that carries session data between the client and computing resource:
- Citrix
- Independent Computing Architecture (ICA)
- Enlightened Data Transport (EDT)
- VMware
- Blast Extreme
- PC over IP (PCoIP)
- Microsoft
- Remote Desktop Protocol (RDP)
The session protocols listed above minimize and compress the data that is transmitted to and from the user device in order to provide the best possible user experience. For example, if a user is working on a spreadsheet within a VDI session, the user transmits mouse movements and keystrokes to the virtual server or workstation, and bitmaps are transmitted back to the user device. Note that the data itself does not populate the user display, but instead bitmaps representing the data are shown. When a user enters additional data in a cell, only updated bitmaps are transmitted.
We @layots are partner with all prime players in the VDI market. Educating the customer and sizing the perfect solution for the customer which best matches the organisation requirements is the primary focus. To know more about this solution, PING US !!!





